Cyber Threat Intelligence – Minority Report
Threat intelligence (TI) is at the maturity level to become a decision making tool. TI refers to evidence based information including context such as mechanisms, Indicators of Compromise (IOC), Indicators of Attribution (IOA), implications and actionable advice about existing or emerging hazards to assets. TI allows the technical staff professionals to make better decisions and take action accordingly.
Historically, intelligence tactics, techniques & procedures (TTPs), as well as various types of intelligence operations, existed long before cyberspace was conceived. Intelligence is often seen as “offensive” in nature when viewed through the lens of spying. The ultimate purpose of TI is actually to enable the CISO or the CIO to make a decision based on evidence and the SOC entities to defend against attack before is materialized.
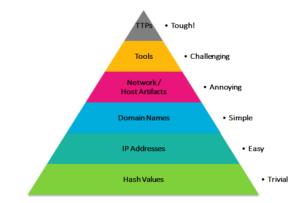
There is a correlation between the type of the IOC’s, the potential of usefulness and difficulty to obtain the necessary data. The base of the pyramid starts with unique signatures of files such as MD5, SHA1 etc. While they are easy to find and share, they are less effective in the long run. On the other hand, the top of the pyramid refers to TTPs, which are more complicated to find and learn, but much more effective in deface prospective.
TI supports decision makers as it allows coping with a threat before it becomes an incident. In addition, it offers the ability to manage and contain the attribution of the threat, and not only the tactical aspect or means. Those advantages provide the defender with a working process and mechanism that is well customized and designed for his organization by covering their needs, assets and working procedures.
It is a known customary practice that security organizations and agencies put a lot of effort into keeping intelligence to themselves, and protect it from leaking out. The concept of information compartmentalization is the basic common practice of these types of organizations. When we look at the necessary practice for cyber security, we find that it is the other way around. Sharing information rapidly and to a wide audience is more efficient & effective to improving your understanding and defending abilities.
Lastly, we see that sharing information from bottom up is another key element. The free flow of information from an organization to the cybersecurity global ecosystem, by using platforms such as MISP (as will be further explained), is highly recommended. By following the Traffic Light Protocol (TLP) we can find it as a win-win opportunity that will upgrade the data & information into knowledge.
Why Is Cyber Threat Intelligence Necessary?
From the Movie Minority Report “In a future where a special police unit is able to arrest murderers before they commit their crimes”, this provides a narrow window of time for the defend forces (police) the time to prevent an event to become an incident.
Cyber events are not limited to companies, sectors or states. Today it is possible to learn from historical cyber events and protect yourself accordingly before the threat reaches your organization. This can be done by detecting and identifying the threat beforehand.
TI is often considered as a collection of “IOC’s or actionable information”, or limited to information about specific security threats. However, there is much more to the story. If an organization does not first understand its assets, infrastructure, personnel & business operations, it cannot understand if the data presents opportunities for malicious actors to attack. Cyber TI can help identify and address potential vulnerabilities in our operations and prepare accordingly.
In the past, security organizations’ efforts involved keeping information to themselves. Today, sharing actionable information (without the identity of the organization been attack) is the most efficient defense mechanism available (i.e. FIRST, MISP etc.).
The fruitful cooperation between companies & organizations is an example for one of the leading defense tools there is in the world. Organizations hire cyber threat intelligence analysts or engage with threat intelligence service providers to perform the task of identifying potential risks and threats in an organization. Cyber threat analysts conduct digital forensics, and adversary targeting to identify, monitor, assess and counter the threat posed by foreign cyber actors against information systems, critical infrastructure and cyber-related interests.
Since one service is related to multiple suppliers – for example ATM or credit card kiosks for a supermarket that reflect Banking, Energy, ISP, Land lines etc. – the defense for that service is based on mutual information sharing for all relevant sectors just to protect one service.
EY presents[2] a hypothetical adversary life cycle. By using this model, TI can help the cyber security team understand which level of the incident they are at. The first and basic phase starts with intelligence gathering.
In the SANS’s 2017 Threat Landscape Survey,[3] includes about 600 cyber security experts from various organizations, the respondents responded on their TI teams and abilities. Among the conclusions, we can find fruitful food for thoughts.
The following charts emphasize how TI is implemented and in which scope among the organizations, while the majority use or plan to use TI as part of their activities.
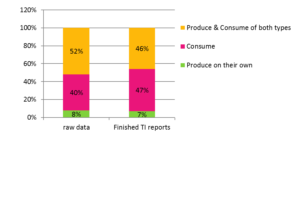
Organizations produce and purchase TI data, whether some of it is raw or finalized intelligence. 60% of organizations produce their TI raw data while more than 90% consume commercial data:
According to the survey, there are different kinds for organizations TI sources. Over 70% of the TI data sources come from industry & community groups like CERTs or ISACs
Organizations have different type of TI dedicated teams. Almost 50% have a dedicated team for this task.
While in most cases, the TI team is part of the cyber security team.

From the survey, we can learn that most organization are using or planning to use TI as part of their operation.
A IHS Markit’s report from October 2016 investigated end-users in a variety of organizations, found the following[4] –
Automated Platforms for TI Sharing
Timing is an additional element for improving your intelligence as working with automated process for sharing and enrichment becoming the basic practice. MISP[5] is a leading platform for sharing TI among national CERTs, CSIRTS and over 2,500 organizations worldwide. Another leading tool is IntelMQ[6].
One of the goals of organizations is reducing the amount of unknown unknowns. Automated platforms can contribute with gathering information from both “official” national CERTs, as well as commercial corporates. The question of reliability of the information is mandatory as at the end we would like to reduce the amount of false-positive results. Over time we can see that some organizations, governmental or not, can provide better intelligence or less. Each organization has its own responsibility to create their policy for verifying and vouching what to consider as part of their working process.
MISP is an open source platform and allows any organization to store and analyze their IOCs. One of the advantages is the ability to connect and share your information among other users and organization. This option is important as the users can enrich his information and find more relevant data which will provide a deeper analysis of the incident.
Being an open source platform, there are many plugins and add-ons available. One example is the ability to import and export the data in various known formats such as CSV, JSON, XML.
In the end, these platforms may be used to support decision makers and improve the intelligence process.
Essential Skills
Cyber threat analysts are professional intelligence officers who apply their analytics, scientific and technical knowledge to solving complex independent variables on a certain research question, produce short-term & long-term written assessments and brief the organization. This work demands initiative, creativity, analytical skills, and technical expertise.
However, the most important requirement for intelligence analysis is analytical skill. At times, this skill is more of an art form than a hard science. However, it can be developed and improved in a few ways. First, it requires an analyst to become a technical expert in interdisciplinary expertise. Unfortunately, many analysts who are just starting out feel that intelligence tradecraft is a “fuzzy” field in which people without technical skills can still be experts. As they work in the field, however, they will find that the opposite is actually the case: cyber threat intelligence analysis, when performed correctly, is also very demanding from a technical perspective. A good analyst should be able to pick out what is obviously true or obviously false almost instantly based on automation, scoring system etc.
In Conclusion
The growth and sophistication of cyber-attacks against each and every one of us has turned Threat Intelligence from a luxury to a necessity. TI allows organizations to go beyond just collecting data about their threats, but also get to know them, be aware of what they are confronting with, maximize security, and pinpoint reconnaissance and weaponization methods before the breach occurs.
The moment the organization directs it, the real challenge is to analyze the data.
There is a multitude of TI sources, and many security tools are able to incorporate some sort of processed TI. However, if you want to do it professionally and tailored, you must have dedicated TI analysts. A well-equipped analyst, armed with this intelligence, can understand how the adversary relates to the target environment and know what he is capable of and what methods he uses.
So, whether your enterprise is small or large, public or private, financially motivated or working for the good of mankind, TI has become something that is necessary, inevitable, committed to reality and a decision making tool. It is also not going to change anytime soon.
[1] http://detect-respond.blogspot.co.il/2013/03/the-pyramid-of-pain.html?m=1.
[2] http://www.ey.com/Publication/vwLUAssets/EY-cyber-threat-intelligence-how-to-get-ahead-of-cybercrime/$FILE/EY-cyber-threat-intelligence-how-to-get-ahead-of-cybercrime.pdf
[3] https://www.sans.org/reading-room/whitepapers/awareness/defending-wrong-enemy-2017-insider-threat-survey-37890
[4] https://www.youtube.com/watch?v=LIvvQoceDKk