Chinese hacking group poses as Iranian while conducting cyber espionage in Israel: US Firm
Security firm FireEye reported that a Chinese hacking group has been posing as Israel’s geopolitical adversary, Iran and conducting cyber espionage by hacking into government and telecommunication networks in Israel. FireEye, in a report, stated that the hacker group, which they identify as “UNC215”, has been carrying out sustained spying efforts and activities in Israel while posing as Iranian operatives. The group embedded the malicious code in Farsi, the predominant language in Iran, and planned to use the Modus Operandi in efforts across West and Central Asia. UNC215 used Remote Desktop Protocols (RDPs) to steal credentials from trusted third parties, according to the report. RDPs grant an intruder access to a system remotely, giving them a view of the desktop of a connected device from afar. The FireEye report also states that the UNC215 has been carrying out attacks against the Israeli government institutions, IT providers and telecommunications entities since January 2019.
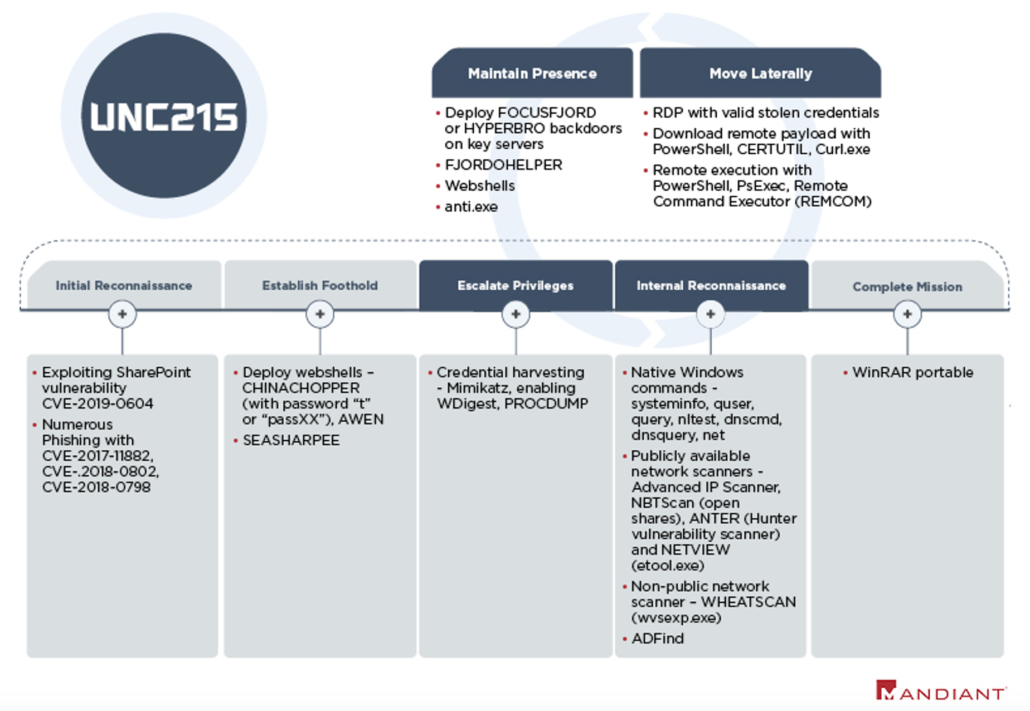
This development raises the issue of false flag operations, where a group tries to hide its identity and blame another entity for the intrusion. While the investigative agencies initially believed that an Iranian group carried out the intrusions and espionage because the hackers wrote in Farsi and used tools usually associated with Iranian hacking groups. However, evidence and information gathered from other cyber-espionage cases revealed that the group responsible originated from China. The cybersecurity landscape is complicated, and attributing an attack to an entity or a country is challenging. Misattributions are very common, and hacking groups use various ways to hide their identities, including very basic methods like writing code comments in a particular language. It’s easy to hide identity in isolated incidents; however, it becomes more difficult as the number of attacks increases.
FireEye stands by its report. Meanwhile, a Chinese spokesperson at the Washington embassy challenged the findings. Liu Pengyu said, “Given the virtual nature of cyberspace and the fact that there are all kinds of online actors who are difficult to trace, it’s important to have enough evidence when investigating and identifying cyber-related incidents”. The Middle East Institute’s cyber program chair also said that the findings may not be entirely conclusive and that FireEye was in no position to make attributions in the absence of a thorough government investigation.
Chinese cyber-espionage attempts are nothing new. For example, the US had charged Chinese tech giant Huawei in a case where they were accused of stealing trade secrets from T-Mobile. In addition, China has used cyber theft as a part of its national strategy and as a vehicle to accelerate its development. However, this incident begs the question of what China’s intention might be while going after an important partner like Israel, where it invested around $11.6 Billion in high-tech startups. One belief is that China’s impunity is bolstered by an inflated sense of self-importance and the economic hold over other states. Another assertion is that China merely wishes to stir up trouble among essential partners of the US. Although the intentions of the Chinese may be up for debate, their method of operation and supporting hacking groups which cause damage, nuisance and theft in other states is widely known. Once the attribution of the attack is more transparent, it would be interesting to see how other states respond to China.

